Introduction to Certificate Authority Authorisation (CAA)
2017.09.05
What is Certification Authority Authorisation?
Certification Authority Authorisation is a standard that allows a DNS domain name holder to authorise one or more Certification Authorities (CAs) to issue TLS certificates for that domain. The use of CAA allows a public Certification Authority to implement additional controls to reduce the risk of unintended mis-issuance of TLS certificates.
Certification Authority Authorisation is a standard defined by the Internet Engineering Task Force (IETF) and described in RFC 6844. It is mandatory for all publicly trusted CAs to implement and support this standard from September 8th 2017 Read details here.
Why use CAA?
Historically, there has been no constraints on which domains a Certificate Authority is allowed to issue TLS certiicates for. Even though the CAA standard has existed for some years already, it has not been mandatory for a CA to follow this standard and check CAA at time of issuance.
By using Certification Authority Authorisation, the domain owner may authorise one or more specific CAs to issue TLS certificates for that domain and by implication, no other CAs are authorised. Thus CAA protects websites by preventing the issuance of rogue or unauthorised SSL/TLS digital certificates, e.g. by preventing attackers to use any other CAs with weak controls.
The domain owner might add or remove authorised CAs at any time and is free to authorise several CAs to issue TLS certificates for the domain. If no specific CA is authorised by means of CAA, any CA is allowed to issue certificates for the domain.
How CAA works
Certification Authority Authorisation uses the Domain Name System (DNS), the system on internet that converts a domain name to a physical address. When you enter www.buypass.com in your browser, DNS translates this domain name to the IP address for the server providing the Buypass’ services.
CAA is implemented by using DNS Resource Records (RR) and it is the domain owner who manages these records. The domain owner may do this himself or may delegate the management to his DNS provider.
CAA RRs are published in DNS and managed similarly to other DNS Records (like MX, CNAME etc). It includes a <tag,value> pair called a property and there is also a flag indicating how critical the property is.
A CAA RR might look like this:
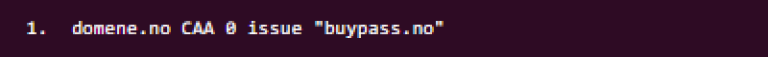
This RR is defined for the domain ‘domene.no’ and CAA specifies that this is a CAA Resource Record. ‘0’ is the flag, ‘issue’ is a tag and ‘buypass.no’ is the value in this property.
This specific CAA RR authorises Buypass to issue TLS certificates for this domain, including all subdomains. If this is the only CAA RR specified for the domain, no other CA is allowed to issue certificates for the domain. The domain owner might add additional CAA RRs authorising other CAs to issue for the domain as well. Each publicly trusted CA has defined a set of Issuer Doman Names which the CA recognises as identifiers within CAA RR. i.e. meaning that the holder of these Issuer Domain Names is authorised to issue for the domain.
Tags
RFC 6844 defines 3 different CAA RR tags to be used, they are issue, issuewild and iodef.
issue specifies the CAs authorised to issue TLS certificates for the domain and there might be multiple CAA issue RRs.
This might look like:
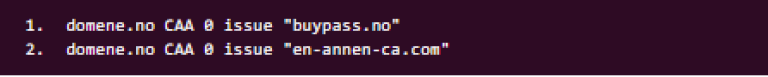
This authorisation is valid for the given domain and all subdomains, including wildcard domains (unless issuewild also is specified, see below). It is also possible to use this tag to specify that no CA is allowed to issue certificates for this domain at all by using an “empty” value like this:

issuewild specifies the CAs authorised to issue TLS wildcard certificates for the domain and this tag use the same syntax as issue, e.g.

If issue is specified for a domain but not issuewild, then the issue property is also valid for wildcard domains. If both issue and issuewild is defined, issuewild is used for wildcard domain names, while issuewild is ignored for any other domain name. iodef specifies a method for reporting unauthorised certificate applications to the domain owner. This might look like this:
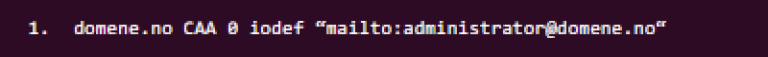
In this example, the domain owner can be contacted at the email address administrator@domene.no.
Buypass uses iodef and will report certificate applications for which Buypass is not authorised by using the email address in the mailto: element in iodef. It is good practice for a domain owner to include a method for contacting him by defining this in iodef. But ensure that these contact information is correct and kept up to date so such reports are properly handled.
Which domain names identify Buypass as issuer?
Buypass uses the domain names ‘buypass.no’ and ‘buypass.com’ as Issuer Domain Names in CAA. If any of these domain names are used as value in an issue or issuewild CAA RR, we recognise this as Buypass being authorised to issue certificates for the domain.
How to authorise Buypass to issue TLS-certificates for your domain?
To ensure that Buypass is authorised to issue TLS certificates for your domain, you should use Certification Authority Authorisation and specify this in the CAA Resource Records.
If you manage DNS records for your domain yourself, you must specify ‘buypass.com’ or ‘buypass.no’ as values in CAA RRs using the issue and/or issuewild tag. This ensures that Buypass is authorised to issue certificates for this domain. Vi recommend you to specify the following CAA Resource Records:
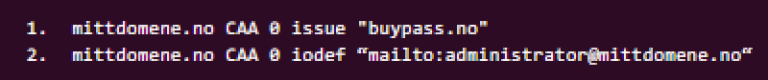
This authorises Buypass to issue TLS certificates for this domain, including subdomains and wildcard domains. If you want to be explicit about issuing wildcard certificates, you may specify this by an additional CAA RR:
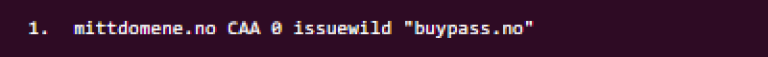
But this is also covered by the issue CAA RR as defined above. You might also use this tag to specify that no CAs at all are allowed to issue wildcard certificates for your domain. This can be accomplished by his CAA RR:
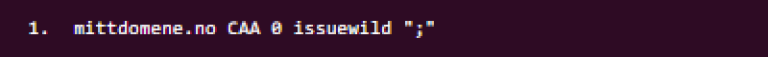
If you want to authorise more CAs to issue certificates for your domain, you simply add additional issue (or issuewild) CAA RRs using the other CAs Issuer Domain Names. Contact your DNS provider or internet service provider for assistance with setting the DNS CAA RR for your domain if you are unable to do this yourself.














